privacy
Rules (WIP)
- No ad hominem allowed
- Attack the idea, not the poster
privacy has nothing to do with having something to hide. Instead, privacy means protecting the human being that you are, all the personal details that make you, you. What you care about, what you love, what you hate, what you are curious about, what makes you laugh, what you fear. And most importantly, choosing when you decide to share that information and who you share it with.
it is possible to build technology used by millions of people with privacy at the heart. We build technology to advance that right in order to help users reclaim their agency in digital spaces.
(But by default, Tor Browser is not shipped with uBlock Origin.)
PS: ONION LINK http://pzhdfe7jraknpj2qgu5cz2u3i4deuyfwmonvzu5i3nyw4t4bmg7o5pad.onion/tor-in-2023/index.html
NOTE: This is about the Fifth Amendment protection against self-incrimination after a search warrant for someone’s cell phone is procured; not about digital privacy in general at the U.S. Border (a warrantless search).
See also: https://monero.town/post/1134494 EFF to Supreme Court: Fifth Amendment Protects People from Being Forced to Enter or Hand Over Cell Phone Passcodes to the Police
Now before the House, HR 6570 proposes to reauthorize Section 702 for three years — but with reforms including requiring all US intelligence agencies to obtain a warrant before conducting a US person query.
a competing bill, the FISA Reform and Reauthorization Act of 2023 (HR 6611), doesn't include a warrant requirement — and, in fact, includes language that many worry could be used to force private US companies into assisting in government-directed surveillance
House Intelligence Committee bill would also expand the definition of an electronic communication service provider include a broader range of providers, including those who “provide hardware through which people communicate on the Internet.”
See also: Tell Congress: They Must Defeat HPSCI’s Horrific Surveillance Bill | EFF Action Center
Bis zum Jahr 2030 will die EU allen Bürger:innen eine „European Digital Identity Wallet“ (ID-Wallet) zur Verfügung stellen. Sie soll on- wie offline bei Verwaltungsgängen und Bankgeschäften, aber auch bei Arztbesuchen, Alterskontrollen oder beim Internetshopping zum Einsatz kommen.
(By 2030, the EU wants to provide all citizens with a “European Digital Identity Wallet” (ID wallet). It is intended to be used online and offline for administrative procedures and banking as well as medical visits, age verification, and internet shopping.)
The article (in German) is mostly about eIDAS 45
Cf. https://monero.town/post/1018961 Last Chance to fix eIDAS: Secret EU law threatens Internet security
(There are many English articles about it; see e.g.
https://mullvad.net/en/blog/eu-digital-identity-framework-eidas-another-kind-of-chat-control )
Though not the main topic of the article, this “ID wallet” thing sounds disturbing. (EU politicians calls a normal wallet “unhosted wallet” and don’t like it very much.)
Many countries use censorship systems to block access to human rights resources
.onion sites are particularly useful at maximizing internet users' privacy and anonymity because they never leave the Tor network.
While technically I2P might be better, it’s good news that a recognized human rights organization has adopted an onion, because that will improve the “shady” image of Tor, esp. hidden services (aka darknet), as in “privacy technology is good, not for criminals, but for you, for everyone. Using Tor is normal, and Monero is a great tool.”
Retroshare establish encrypted connections between you and your friends to create a network of computers, and provides various distributed services on top of it: forums, channels, chat, mail... Retroshare is fully decentralized, and designed to provide maximum security and anonymity to its users beyond direct friends. Retroshare is entirely free and open-source software. It is available on Android, Linux, MacOS and Windows. There are no hidden costs, no ads and no terms of service.
law enforcement has been using […] systems since 2015, in utmost secrecy. The software in question […] can track a person across a network of cameras, for instance, by the color of their sweater
Any policeman […] can request to use [it]
The potential use of facial recognition worries within the institution itself. […] In France, facial recognition is only authorized in rare exceptions
This massive installation was carried out outside the legal framework provided by a European directive and the French Data Protection Act
The National Commission on Informatics and Liberty (CNIL), a French administrative regulatory body, started an investigation against the French Minister of the Interior [1][2]. The Minister, Gérald Darmanin ordered an investigation [2].
- [1] https://nitter.oksocial.net/CNIL/status/1724745047537488019 [French]
- [2] https://web.archive.org/web/20231121093507/https://www.ouest-france.fr/politique/gerald-darmanin/entretien-gerald-darmanin-lantisemitisme-le-signe-dune-societe-qui-ne-va-pas-tres-bien-938b76ce-856c-11ee-9632-b62f00689e79 [French]
La Cnil […] annonce l’ouverture d’une enquête contre le ministère de l’Intérieur. Elle soupçonne la police d’utiliser un logiciel de reconnaissance faciale, depuis 2015, en dehors de tout cadre légal. Qu’en est-il ?
(CNIL suspects the police are using facial recognition outside any legal framework. Comments? - Gérald Darmanin’s answer: The news is true. I ordered an investigation.)
the White House has, for the past decade, provided more than $6 million to the program, which allows the targeting of the records of any calls that use AT&T’s infrastructure
the program takes advantage of numerous “loopholes” in federal privacy law
the DAS program has been used to produce location information on criminal suspects and their known associates, a practice deemed unconstitutional without a warrant
(This website is a bit annoying.)
Onion http://rurcblzhmdk22kttfkel2zduhyu3r6to7knyc7wiorzrx5gw4c3lftad.onion/
This free email provider is not for everyone. Sometimes a Cockmail address is not accepted to register something. Sometimes, though not often, another email provider may indiscriminately block email from Cock.li. Afaik Cock.li<->Proton, Cock.li<->Tuta work.
PS: Admin, Vincent Canfield @[email protected]
In celebration of Bitcoin Black Friday 2023, we're offering a 10% discount on all BusKill cables sold between Nov 18 to Dec 03.
 |
|---|
| BusKill Bitcoin Black Friday Sale - Our Dead Man Switch Magnetic USB Breakaway cables are 10% off all orders paid with cryptocurrency |
What is BusKill?
BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer.
 |
|---|
| Watch the BusKill Explainer Video for more info youtube.com/v/qPwyoD_cQR4 |
If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device.
What is Bitcoin Black Friday?
Black Friday is ~1 month before Christmas, and it's the busiest shopping day in the US. The first "Bitcoin Friday" (launched by Jon Holmquist) was Nov 9th, 2012 (at the time, one bitcoin was ~$11). The following year, the two ideas merged to become Bitcoin Black Friday.
This year, we're joining Bitcoin Black Friday by offering our products at a 10% discount if you pay with cryptocurrency.
Why should I use cryptocurrencies?
We've always accepted cryptocurrencies because:
- They're more secure than pre-cryptocurrency payment methods
- They're a more egalitarian system than pre-cryptocurrency finance
- They're more environmentally friendly than pre-cryptocurrency financial systems
- The fees are less than pre-cryptocurrency transactions
- They allow for anonymous purchases online
- Their transactions are censorship-resistant
Security
Before cryptocurrencies, making an online transaction was horrendously insecure and backwards.
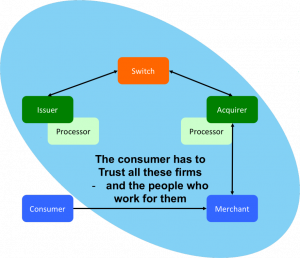 |
|---|
| "Conceptually, pull-based transactions are really not that different than giving three parties the password to your online banking service and trusting them to log in and take what they need. You have to trust the merchant, their IT supplier; the acquiring bank, their third-party processor; the card network; and your own card issuer---and everybody who works for them and has access to their systems. If a bad guy gets hold of your card details at any point in this process, they could drain your account. |
| The picture shows the scope of all the entities with access to your critical card information" source |
Asymmetric cryptography has been available since the 1970s, but CNP (Card Not Present) transactions to this day still don't use public keys to sign transactions. Rather, you give your private keys (that is, your credit card number, expiry, etc) directly to the merchant and you authorize them to pull money out of your account (trusting that they take the right amount and not to loose those precious credentials).
Bitcoin flipped this around to actually make transactions secure. With bitcoin, you don't give others the keys to take money out of your account. Instead, transactions are push-based. You sign a transaction with your private keys, and those keys are shared with no-one.
Even today, pre-cryptocurrency transactions are abhorrently insecure. In the US or Europe, if someone knows your account number and bank, they can direct debit money out of your account. For the same reason, losses due to credit card theft is enormous. To quote Satoshi Nakamoto's criticism of pre-cryptocurrency transactions, "A certain percentage of fraud is accepted as unavoidable"
In fact, fraudulent transactions in the banking industry are so common that your bank will generally reimburse your account for any malicious transactions that you tell them about within 60-90 days. But if someone drains your account of all your money and you don't notice for 12 months? Too bad. All your money is gone.
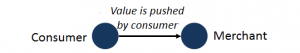 |
|---|
| In Bitcoin, transactions are push-based. source |
Tokenization and 3DS are merely bandages on a fundamentally backwards, pull-based transaction model. But because bitcoin is push-based, it's magnitudes more secure.
Egalitarian
If you have a bank account, then you probably take a lot of things for granted. Like buying things online (with a credit card). Or getting cash when traveling abroad (from an ATM machine). Or taking out a loan so you can start a business.
Before crypto-currencies, it was very difficult to do these things unless you had a bank account. And in 2008 (the year with the first-ever bitcoin transaction), McKinsey & Company published a report concluding that half of the world's adult population is unbanked.
But with crypto-currencies, anyone with access to the internet and a computer or smart phone can use bitcoin to send and receive money online -- without needing to first obtain a bank account.
Environmentalism
The energy required to facilitate transactions in decentralized, blockchain-based cryptocurrencies like bitcoin is minuscule by comparison. And, most importantly, the amount of energy used to solve the proof-of-work problem does not grow as the number of transactions-per-second grows.
Traditional financial institutions require an enormous amount of overhead to facilitate transactions in their centralized networks. Unlike bitcoin, which was designed specifically to eliminate the unnecessary overhead created by a trusted third party, pre-cryptocurrency transactions required humans to verify transactions. These humans require office buildings. These office buildings require energy to build and maintain. And, most importantly, as the number of transactions-per-second grows on their network, the number of humans and office space also grows.
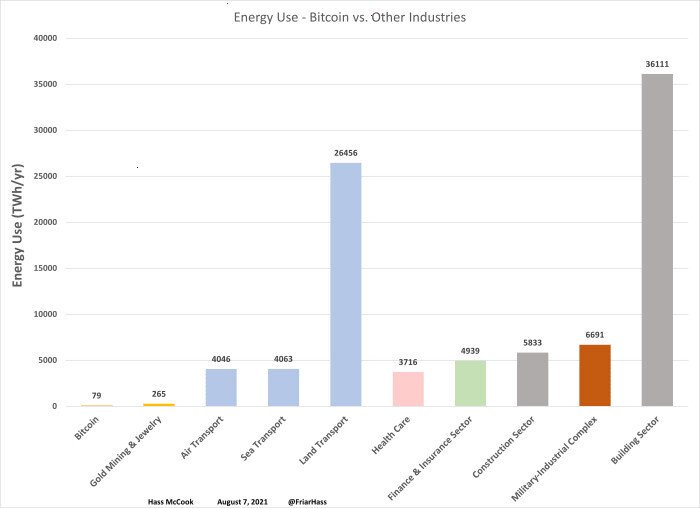 |
|---|
| Bitcoin versus other industries |
yearly energy use, in TWh source |
This fact is often misunderstood because there's a lot of misinformation on the Internet that makes a few disingenuous modifications to the facts:
- They calculate the energy usage of the computers processing transactions only, maliciously omitting calculating the energy usage of the entire industry's infrastructure (eg energy used by office buildings)
- They calculate the energy usage per transaction, maliciously omitting the fact that the amount of energy expended by bitcoin miners is automatically adjusted by the proof-of-work algorithm (so energy usage does not increase as the network scales-up)
- They offer statistics about "energy usage" without mentioning the energy sources. It matters if the energy source is coal/nuclear/natural-gas or solar/wind/hydroelectric
"...estimates for what percentage of Bitcoin mining uses renewable energy vary widely. In December 2019, one report suggested that 73% of Bitcoin's energy consumption was carbon neutral, largely due to the abundance of hydro power in major mining hubs such as Southwest China and Scandinavia. On the other hand, the CCAF estimated in September 2020 that the figure is closer to 39%. But even if the lower number is correct, that's still almost twice as much [renewable energy sources] as the U.S. grid" source: Harvard Business Review Nic Carter
The facts are that the energy usage of bitcoin is magnitudes less than the energy used by pre-cryptocurrency financial intuitions, that energy usage does not increase as the number of transactions processed by the network increases, and that mining bitcoin is often done with renewable energy.
The facts are that the energy usage of bitcoin is magnitudes less than the energy used by pre-cryptocurrency financial intuitions, that energy usage does not increase as the number of transactions processed by the network increases, and that mining bitcoin is often done with renewable energy.
Low Fees
The introduction to the Bitcoin White Paper (2008) clearly states that Bitcoin was created to reduce costs by using a distributed ledger (the blockchain) to eliminate the need for a trusted third party.
"Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs... These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions." source: Bitcoin Whitepaper Satoshi Nakamoto
At the time of writing, the average transaction fee for a bitcoin transaction is $0.06. And unlike pre-cryptocurrency transactions, you can increase or decrease the fee that you pay to increase or decrease the time it takes for the transaction to complete (at $0.06, it will get added to the blockchain in ~1 hour).
By comparison, the way to send funds internationally through the Internet via pre-cryptocurrency banks is via an international wire transfer. Fees very per bank, but they typically charge $15-$85 per transaction. And unlike bitcoin, wire transfers won't make move on nights and weekends, so they can take 1-7 days to complete.
Also, with bitcoin, that $0.06 transaction fee only applies when you're sending money. Many banks will also charge a fee for an incoming wire transfer. In bitcoin, there is no transaction fee to receive money.
Anonymity
Though early cryptocurrencies like Bitcoin don't ensure anonymity like newer privacy coins, ZCash and Monero were designed specifically to provide private transactions.
This allows our customers to purchase from us anonymously, which can be extremely important for activists and journalists whose lives are threatened by their adversaries.
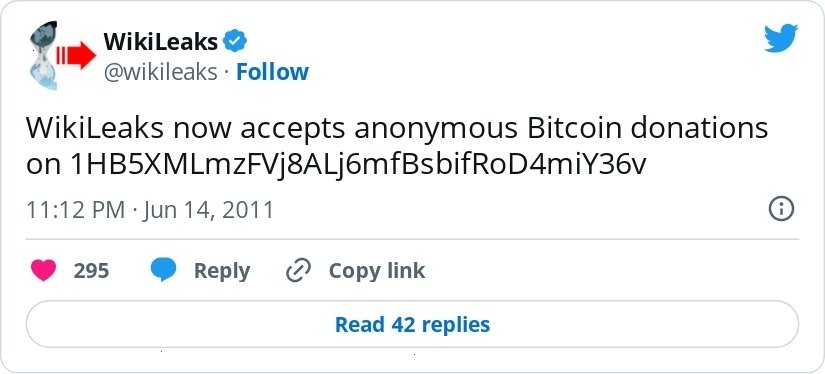 |
|---|
| WikiLeaks started accepting donations in Bitcoin 7 months after PayPal froze their account |
We accept both ZCash and Monero. If you'd like us to accept another privacy coin, please contact us :)
Censorship-Resistant
Cryptocurrencies like bitcoin are peer-to-peer and permissionless. Transactions exchanging bitcoins occur directly between two parties. There is no middle-man that has the power to block, freeze, or reverse transactions. Before blockchains were used to maintain a public ledger and enable peer-to-peer transactions, we were dependent on big financial institutions to move money on our behalf through the internet. That antiquated system allowed them to censor transactions, such as donations made to media outlets reporting war crimes and donations to protest movements.
"For me, that is one of the coolest things about bitcoin... People can potentially use it donate more anonymously to dissident groups and causes in a world where mass government surveillance threatens freedom of expression and certainly harms activists' ability to fundraise for their work, when people are afraid they could be targeted by a government for donating to a worthy cause." source Evan Greer
After PayPal froze WikiLeaks's donation account in 2010, WikiLeaks started accepting bicoin in 2011. From Occupy Wall Street to Ukraine, defenders of democracy have utilized permissionless cryptocurrencies to accept international donations without the risk of transactions made through financial institutions.
Buy BusKill with crypto
Don't risk loosing your crypto to a thief that steals your laptop. Get your own BusKill Cable at a 10% discount today!
Buy a BusKill Cable
https://buskill.in/buy
You can also buy a BusKill cable with bitcoin, monero, and other altcoins from our BusKill Store's .onion site.

Stay safe,
The BusKill Team
https://www.buskill.in/
http://www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion
See also: Fifth Circuit says law enforcement doesn’t need warrants to search phones at the border https://monero.town/post/402125
The app store “collects and sends data […] This includes information like device model, brand, country, timezone, screen size, view events, click events, logtime of events, and a unique KID ID,”
Hancock didn’t return the tablet to her daughter until after making changes to protect her daughter’s privacy.
[She] even installed Tor, a browser that is designed to protect the anonymity of its user.
An awesome Mom, like Mrs. Roberts from xkcd!
A storefront, said Ortis, is a fake business or entity, either online or bricks-and-mortar, set up by police or intelligence agencies.
The plan, he said, was to have criminals use the storefront — an online end-to-end encryption service called Tutanota — to allow authorities to collect intelligence about them.
Tutanota (now Tuta) denies this: https://tuta.com/blog/tutanota-not-a-honeypot
These changes radically expand the capability of EU governments to surveil their citizens by ensuring cryptographic keys under government control can be used to intercept encrypted web traffic
This enables the government of any EU member state to issue website certificates for interception and surveillance
The browser ecosystem is global, not EU-bounded. Once a mechanism like QWACs is implemented in browsers, it is open to abuse
https://en.wikipedia.org/wiki/EIDAS
The proposal would force internet companies to place a backdoor in web browsers to let them perform a man-in-the-middle attack, deceiving users into thinking that they were communicating with a server they requested, when, in fact, they would be communicating directly with the EU government. […] If passed, the EU would be able to hack into any internet-enabled device, reading any sensitive or encrypted contents without the user's knowledge
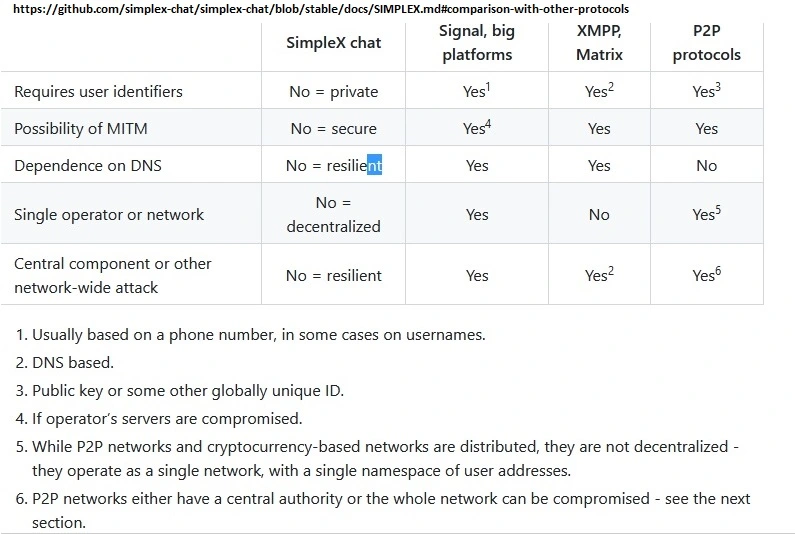
SimpleX Chat is still a relatively early stage platform (the mobile apps were released in March 2022) But in the end, SimpleX will be our choice, right? Or at least for most of us.
here: SimpleX-Chat Github
[Edit 2: Read the admin’s “reasoning” and comments here or see PS below. The clearnet site is up again. The onion versions = 100% up tme for me]
[Edit: As of writing this (2023-11-01) their clearnet server is down, while the onion version is working. Cock.li is exactly like this… Relatively rarely but randomly it’s down. Kind of irresponsible but it’s just like that. Interestingly, though, onion is up and clearnet is down. Usually opposite.]
Onion http://rurcblzhmdk22kttfkel2zduhyu3r6to7knyc7wiorzrx5gw4c3lftad.onion/
Cockbox on kycnot.me - https://kycnot.me/service/cockbox
(From their webpage)
Cock.li is your go-to solution for professional E-mail and XMPP addresses. Since 2013 cock.li has provided stable E-mail services to an ever-increasing number of users. Cock.li allows registration and usage using Tor and other privacy services (proxies, VPNs) and thanks to continued funding by its users is certain to stay free forever.
Cock.li (aka Cockmail) is a Tor-friendly, privacy-focused, soon-to-be-10-year-old free email provider (IMAP, POP, XMPP, Webmail). Although currently (since around 2021) a new registration is invite-only, the admin @vc now states on their website:

E-mail is a Human Right!
Oppressive governments are using dirty tricks to try and force e-mail providers to require phone numbers or other controlled integrations to register. We will never allow these crimes against our userbase. We will stand up for the right to register for e-mail without being surveilled, and demand this right to be recognized globally. Public registration re-opens on cock.li's 10th birthday, 20 November.
Probably people here know this service pretty well, but some important points:
-
Their email addresses are sometimes blacklisted when you want to use them, because in the past the service was abused by spammers. So this provider may not be suitable for normal users/normal usage. Its “technical scores” may be low too, when checked e.g. via https://internet.nl/mail/ If you think this is sketchy and its name is weird, it is. It’s not for you, so please just ignore it.
-
A cock.li account may be great to have if you want to sign up and use it anonymously always via onion (something you can’t do with Proton or Tutanota), perhaps with PGP. Maybe great to use on Tails OS too.
-
Their service was not very stable in the past. In recent years, it’s been rather stable and very fast even via onion. Pop/Imap via Tor works perfectly. Cock.li onion may load 100 times faster than that of Proton.
-
Custom domains are not supported! Consider Disroot or Tutanota if you need them and would like to pay with Monero.
-
They are one of the earliest v3 onion providers. In contrast, Proton was so slow to migrate from v2 to v3 (even after v2 got obsolete). Cock.li is also one of the oldest mail providers that started accepting BTC and XMR donations. So probably they’re extremely well-funded (you know why).
-
If you use Thunderbird, set up your account manually (its automatic setup probably doesn’t work right).
For more info, visit their webpage. Please DO NOT abuse this based cypherpunk service.
PS. Vincent Canfield ([email protected]) wrote on September 23, 2023:
Good morning, CISA is now calling cock.li a "Malicious E-mail Domain" and implies this is because it's not "publicly available". So, cock.li will once again open to the public on its 10th birthday, 20 November. #StopRansomware
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-263a
For those who don't remember, a previous CISA advisory which recommended "service providers strengthen their user validation and verification systems to prohibit misuse of their services" shortly predated cock.li going invite only.
https://www.cisa.gov/news-events/cybersecurity-advisories/aa21-116a
I'm sure if cock.li added phone number verification these joint statements would go away. Everyone sees what's happening, you want to force all providers to link to identities so you can surveil people. Cock.li is never adding that bullshit.

privacy is often considered a tabu when talking about money, despite being a well-accepted fundamental human right for other topics. The growing development of high-surveillance financial tools often creates controversy and conflict of interest against privacy cryptocurrencies.
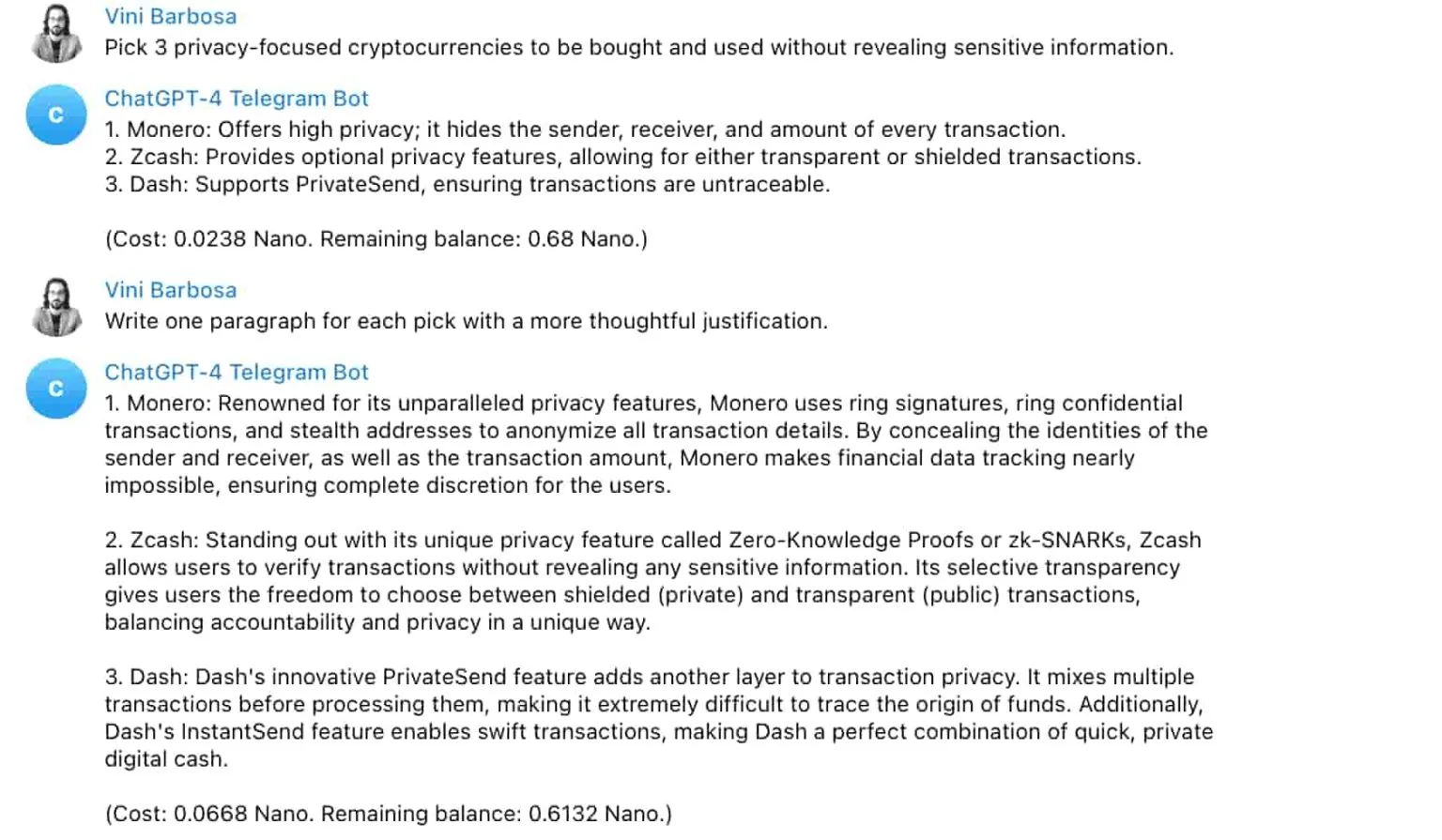
[We] asked ChatGPT to pick three privacy cryptocurrencies:
The AI responded with its top 3 picks being Monero (XMR), ZCash (ZEC), and Dash (DASH).
“Renowned for its unparalleled privacy features, Monero uses ring signatures, ring confidential transactions, and stealth addresses to anonymize all transaction details. By concealing the identities of the sender and receiver, as well as the transaction amount, Monero makes financial data tracking nearly impossible, ensuring complete discretion for the users.”
— ChatGPT-4
Send me your seed words.
"Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say."
—Edward Snowden
1️⃣ Completely normal photos, such as holiday pictures 🏞️ are considered suspicious.
2️⃣ So our private family photos or the chats and pictures from your sexting yesterday 🍑🍆 also end up on an official table. So we can throw privacy in the bin 🚮
Chances are high that most of your European friends have never heard of chat control. So let them know about the danger and what you think about the chat control proposal.
“The European Commission launched an attack on our civil rights with chat control. I contacted my local MEP to tell him that I oppose the proposal. You can do so too! This Website I found will help you write an e-mail to an MEP using A.I.”



